UDP
Right now, the only thing that TraceWrangler can sanitize is the UDP port number. Maybe there will be more options in the future if a need for additional sanitization comes up.
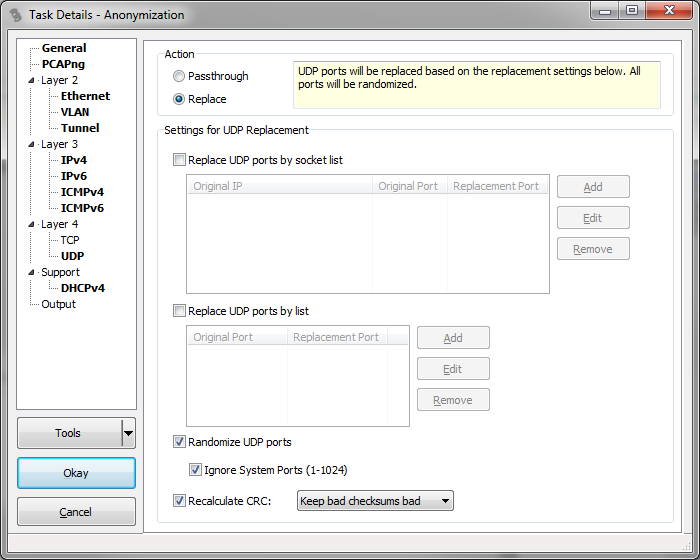
Replace UDP ports by socket list: If a socket is found in a packet that matches the value in the original port column it will be replaced by the value in the replacement port column. This allows very specific port replacements, e.g. if you only want to replace ports for certain IP and port combinations. You can use the popup menu to import and export comma separated port lists to store and reuse ports at a later time.
Replace UDP ports by list: If a port is found in a packet that matches the value in the original column it will be replaced by the value in the Replacement column. You can use the popup menu to import and export comma separated port lists to store and reuse ports at a later time.
Randomize UDP ports: If a port wasn't found in the list and this setting is active, a new random port will be assigned. You can use the checkbox for Ignore System ports (1-1024) to automatically keep any port unchanged that is in the range of system ports.
Recalculate CRC: this works just like the IPv4 setting. Since sanitization may lead to a modified UDP layer, the CRC needs to be recalculated. And in case you want to keep bad checksums bad, TraceWrangler do it the same way as for IPv4, except that for UDP, a checksum of zero will be kept at zero.