PCAPng Settings
The settings in this section work on the extra header blocks that are part of each PCAPng file. Some of them are mandatory, others are optional. The official specification of the file format can be found here. The TraceWrangler setting is either "Passthrough" or "Replace". If "Passthrough" is selected, all settings in the lower pane are simply ignored. PCAPng settings only make sense when the file type is PCAPng, of course, and will be skipped in case of reading other file formats.
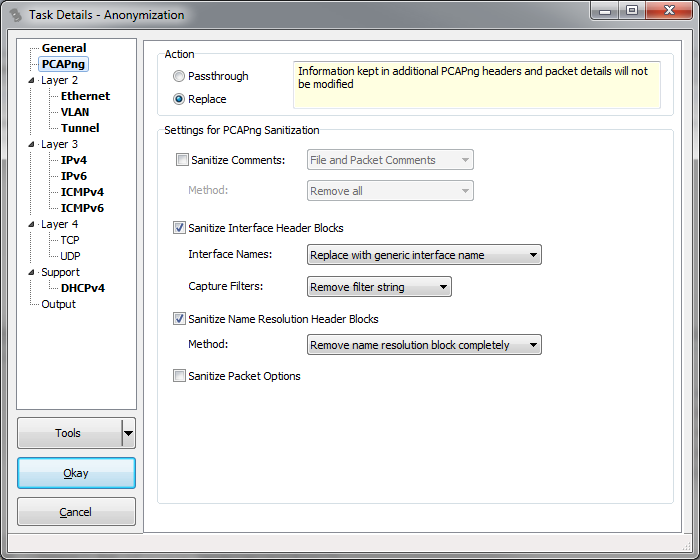
Sanitize Comments: This setting allows removing comments from the file or the packets, or both.
Sanitize Interface Header Blocks: When a capture is taken by dumpcap and written in native PCAPng format, it will write the name of the network card into the mandatory interface description block that is required for each interface that was used in the capture. On Linux, this name is typically something like "eth0", which is pretty nondescript. On Windows, a GUID is created, which could be used to identify the exact interface at a later time because it is highly unique. The options for sanitization are to either keep it as it is, remove it completely by setting the name to an empty string, or to replace it with a generic interface name. The third option will have TraceWrangler create a new random GUID for any GUID it finds and replace the original with it.
The other detail that is written to the Interface Header Block is the capture filter that was used when starting the capture. Since this field may often contain sensitive information like IP addresses that you don't want to expose, the default is to remove the filter string completely. It would be nice to have some sort of automatic replacement of any address found just like when dealing with an IP address in the IP layer, but parsing filter strings can become very complicated, leading to possibly failing to detect sensitive information. So the only options are to remove it or keep it.
Sanitize Name Resolution Header Blocks: PCAPng is capable of keeping a list of FQDNs with their associated IP addresses as they were determined when saving the capture file. This makes it easier to work with traces even when no DNS can provide the name resolution at the time of the analysis, because the file keeps the mappings in the Name Resolution Header Block. Of course, this could not only expose IP addresses you want to sanitize, but also FQDNs of critical systems that you do not want to distribute with the file. Right now, the only option is to completely remove the Name Resolution Block (or keep it, of course).
Sanitize Packet Options: There are a number of optional details that can be stored with each packet, e.g. an MD5 hash. If this setting is active, none of those optional values will be written to the sanitized file.