IPv4
Replacing IP addresses is probably the most common thing that any anonymization tool is going to perform. TraceWrangler tries to make the process as easy to configure as possible, while being as powerful and versatile as possible at the same time. Keep in mind that any IPv4 address that is found in a protocol layer that TraceWrangler can parse and assemble will be anonymized just the same way. Of course that primarily means the IPv4 layer, but also ARP frames, DHCPv4 packets and so on. That is also the reason why there are no IPv4 settings for DHCPv4 and ICMPv4 in their respective sections.
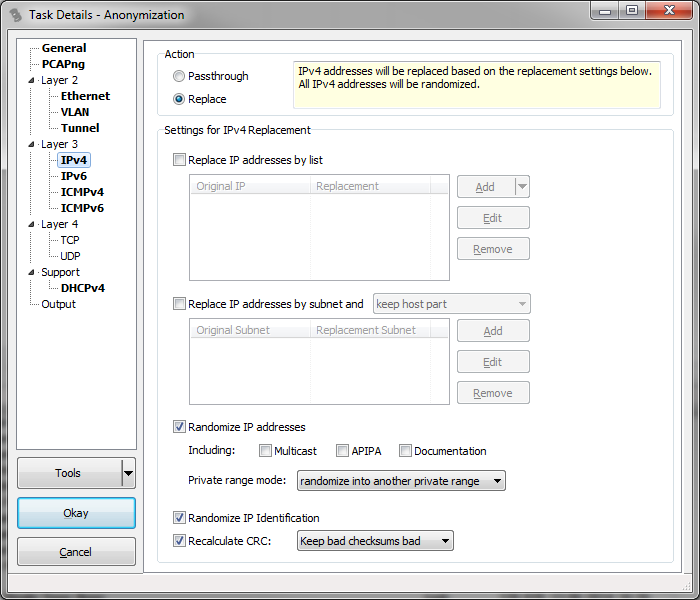
Replace IP addresses by list: if active, any address that is found in the trace that is listed in the IP address list on the "Original IP" column will be replaced wit the according address in the "Replacement IP" column. The "Add" button next to the list is used to add a new replacement pair. A click on the button will open a dialog that allows you to type in an original address to look for, and a second address that will replace the original address if found. There is also a pop up menu to help with adding address replacement pairs, which can be accessed by right-clicking the list:
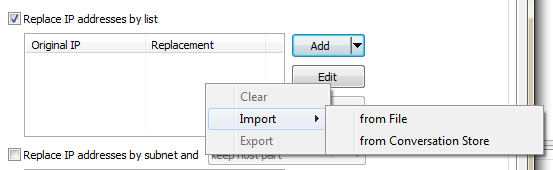
- it is possible to import and export comma separated lists from and to files, in case you want to keep and re-import a list of addresses at a later time. It is also helpful if you want to create replacement pairs in an text editor of your choice and import them.
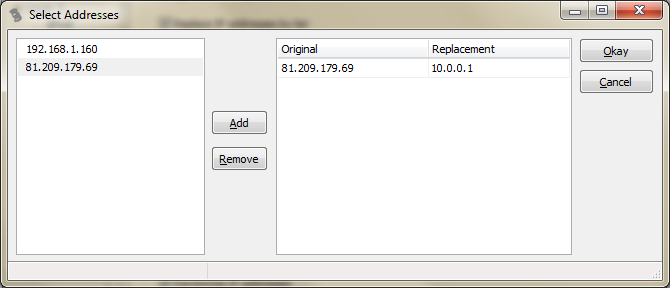
- the Conversation Store is available only if the capture files have been scanned for conversation details before adding/editing the anonymization task. Otherwise the menu option will be grayed out. When selected, another dialog will open to allow selecting and editing replacement IP addresses:
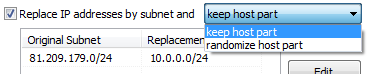
Replace IP addresses by subnet: very often, the primary goal of anonymizing a trace is to hide subnet information, meaning that you do not want anyone to know to which network certain nodes belong. At the same time it can be helpful to keep the host part of each IP intact to preserve address relationships. For this, you can add subnets in CIDR notation (like "192.168.1.0/24"), but you need to enter the same mask bit count for the original network and the replacement network (otherwise the text in the field will be displayed in red).
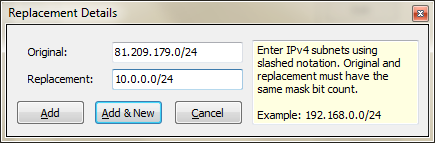
If you choose to replace IP addresses by subnet you can specify what should happen to the host part of the original address. The combo box allows you to chose to keep the host part intact, or randomize it. Just like the IP address list you can use the pop up menu to import and export subnet lists to reuse them at a later time.
Randomize IP addresses: if this setting is active, any address that has not been replaced by either of the lists described above will be randomized. As a sub setting you can force the randomization various special addresses, which will otherwise not be touched and written as their original value to the sanitized file. There are a couple of options to force randomization for specific address types if required:
- Multicast Addresses: Multicast addresses are often reserved for special purpose, which you might want to keep to allow troubleshooting the sanitized file. But even when you force the randomization of multicast addresses TraceWrangler will make sure that the result is once again a multicast address.
- APIPA Addresses: Maybe you've heard the name APIPA, which stands for Automatic Private IP Addressing. Even if you haven't heard that name, you've probably seen an APIPA address, which is in the range of 169.254.0.0/16. Those are usually assigned to network cards when getting an DHCP address fails. Usually they're not giving away any real network and are interesting when seen in a trace because it usually indicates some sort of trouble with DHCP. That's why they should be kept in most cases instead of randomizing them.
- Documentation addresses: There are three special ranges defined for documentation addresses, which means that they can be used as dummy IP addresses in documentation. The ranges are 192.0.2.0/24, 198.51.100.0/24, and 203.0.113.0/24. Since they are dummy addresses they usually do not expose any risk and should be kept intact.
- Private IP Address ranges: IPs in the range of 10.0.0.0/8, 172.16.0.0/12 and 192.168.0.0/16 are private ranges and are not routed over the internet, so exposing them doesn't tell a lot about the network topology. Still it may be desirable to keep the network range a secret if you are afraid that it helps a bad buy with his network reconnaissance. There are three settings for private IP ranges:
- Randomize into another private range: in this case, TraceWrangler will generate a random address, but it will be in a private network range again. That way you keep the fact intact that the address belongs to a private network, without exposing exact details about the network and the IP
- Randomize over full address range: TraceWrangler will randomize the IP address and it is not guaranteed that the IP is a private address afterwards.
- Do not randomize: this setting will keep the original IP address intact.
Generally, randomization will not allow the random result to be any of the following addresses:
- 0.0.0.0
- 127.0.0.0/8
- 255.255.255.255
- the same as the original address
- the same as a replacement address for a different original address
If randomization creates an address from the listed address ranges the dice will be rerolled until it is not on the list anymore. The same will happen when a random result matches an existing replacement IP, because it would be bad if two different original addresses end up being replaced by the same replacement address. It may be very confusing to analyze a sanitized trace in that case, so TraceWrangler will verify each random result to be unique before accepting it.
Randomize IP Identification: some people are concerned that the IP ID can expose information about system behavior, especially when it is counting up by one for each IP packet. With this setting each packet will be assigned a random new IP ID, except fragmented packets. Fragments will also get a new random IP ID, but all fragments belonging together will have their IP ID replaced by the same new random ID to keep their relationship intact.
Recalculate CRC: when the IP layer is changed, for example by replacing IP addresses, the original checksum will not be correct anymore. With this setting you can chose to recalculate the checksum. The combo box allows you to only recalculate checksums if the original checksum had been okay, which is the default. This is another setting that is trying to keep the facts about the original file intact, because it may be interesting for an analyst to know that the checksum had been bad in the original file as well.
To make sure that the checksum is incorrect TraceWrangler does not just use a random number, or the incorrect original, because both may incidentally turn out to be correct. Instead, the correct checksum will be calculated and then forcefully increment it by 1 (and wrapped, if necessary). That way the CRC is incorrect for certain, but you can also tell it was made up because it will always be just 1 higher than the correct would have been.